Ivanti Endpoint Manager Initial Setup for Endpoint Protection
- Tenaka
- Jan 1, 2023
- 6 min read
Updated: Feb 14, 2023
Ivanti's Endpoint Protection's Application Control:
Ivanti Endpoint Protection is a comprehensive security solution that provides organizations with a comprehensive set of security tools designed to protect their endpoints, networks, and data. It is designed to protect users from the latest threats, such as malware, ransomware, and phishing attacks. It also provides advanced capabilities, such as patch management, application control, and user privilege management. With Ivanti Endpoint Protection, organizations can ensure their endpoints are secure and protected from the latest threats.
This article focuses on the initial setup of Ivanti Endpoint Manager and Endpoint Security Application Control, agent deployment and policy. This will provide the bases for the next round of 'verses' articles having thoroughly abused Windows Applocker, WDAC and GPO.
The following has been extracted from the Ivanti Endpoint Protection user guide downloadable from (here).
Ivanti® Endpoint Manager and Endpoint Security for Endpoint Manager consists of a wide variety of powerful and easy-to-use tools you can use to help manage and protect your Windows, Macintosh, mobile, Linux, and UNIX devices. Endpoint Manager and Security tools are proven to increase end user and IT administrator productivity and efficiencyLANDesk
Application control offers the following system-level security:
Kernel-level, rule-based file-system protection
Registry Protection
Startup Control
Detection of stealth rootkits
Network filtering
Process and file/application certification
File protection rules that restrict actions that executable programs can perform on specified files
The initial Ivanti setup focus's on Ivanti Endpoint Protection's (EP) Application Control to compare and pit against Microsoft's Applocker and WDAC. Ivanti's EP Firewall, Device Control and AV policies won't be configured, although it is capable of providing a full management suite of protections from within a single console. The focus is Ivant EP vs Microsoft's application control, the paid 3rd part tools versus the free inbuilt tools.
Ivanti Download:
The good news, Ivanti provides 45 day, fully featured trial software, allowing plenty of time for EP to be put through its paces. The bad news, the trial software is not current, the download is for the 2020.1 version and not the latest 2022.2 or higher. A little sub-optimal considering it's for endpoint protection and security.
Links to access Ivanti Endpoint Manager 2020.1:
45 day trial sign-up (here).
Installation guide (here), Domain with a SQL server is required.
Exclaimers:
After following the installation guide, Ivanti will require a fair amount of fettling to deploy Application Control in enforcement mode. Remember, it's only for application execution to provide a direct comparison to Applocker and WDAC and a baseline reference for EP configuration.
I'm not an Ivanti expert, I've spent a day installing and learning Ivanti. It's expected that the lack of experience with this product results in some ambiguity, I'm not interested in the journey but the net result of trying to exploit Windows with Ivanti Endpoint Protection enabled.
Initial Login:
Let's get to it......
From the Start Menu launch 'Ivanti Management Console', and enter the account details used during setup.
Add LDAP Configuration:
To integrate AD, providing search and deployment of policy, agent and software:
Click on 'Configuration' in the lower left pane.
Right-click on 'Directory' and 'Manage Directory...'
'Add', follow the wizard to include the domain structure using the Domain Admin account.

Initial Agent Audit Policy:
Initially, the endpoint and its software is unknown and an agent is required to be deployed.
Click 'Configuration' in the bottom left windows and then select 'Agent Configuration', then the top left.
In the 'Agent Configuration' window, bottom right, right-click and select 'New Windows agent configuration'.

Update the 'Agent Configuration':
Update 'Configuration Name' with something meaningful.
Check the 'Endpoint Security option.

Browse and then select 'Endpoint Protection' under 'Distribute and Patch' and then 'Security and Compliance'.
Click 'Configure'.

Within 'Endpoint Security' check 'Application Control:' and then click on '....' to configure the Application Control policy.

Select 'Advanced' under 'Application Protection' and click on 'Learning'.
With the initial policy when Ivanti is 'Learning' there is no reason to tempt fate by locking ourselves out of the client.

Select 'Learning' for 'Whitelisting'.

Save the changes and close both the 'Application Control' and 'Agent Configuration wizards.
Agent Deployment:
The agent and EP policy has been created and requires deploying to a client. Ivanti Management is fully featured and comes with LANDesk. For those that aren't familiar it's on par with SCCM\MECM. Here's a guide to assist in deploying the Ivanti agent (here).
For expedience, I've opted for manual agent deployment. Right-click on the new agent and select 'Advance Agent'.

Copy the URL and log on to the Windows 10 or 11 client.
Download the .exe and install.
Both Windows Defender and SmartScreen GPO's required updating to allow the Ivanti agent to install.

Once the agent's installed, launch 'Ivanti Endpoint Security' from the Start Menu for a quick review.
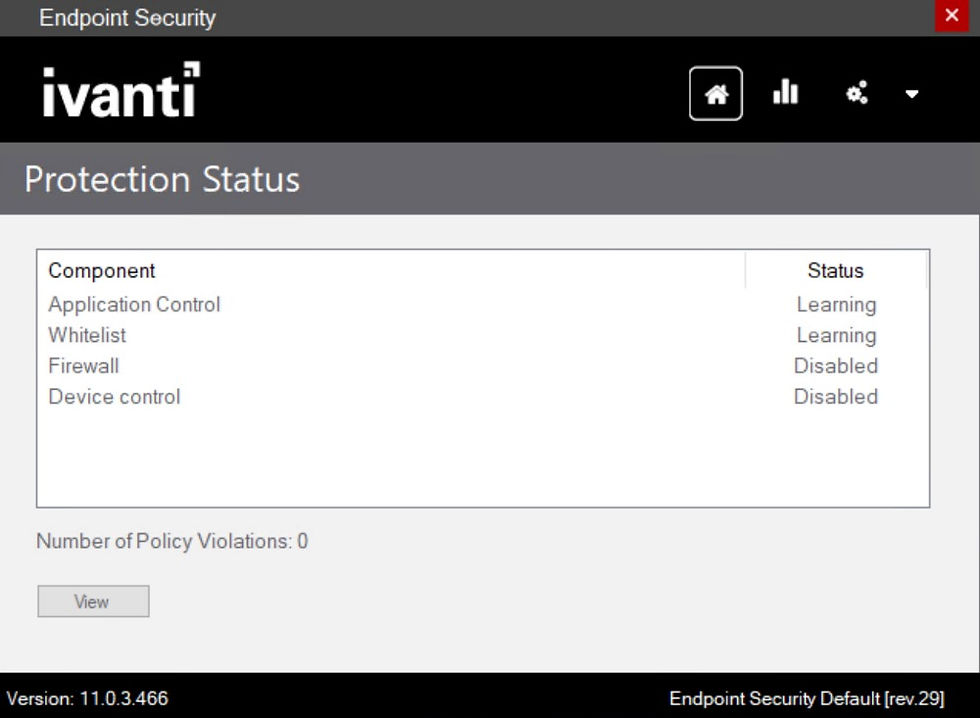
Excellent, Application Control and Whitelist learning policies are in effect.

In preparation for blocking mode, launch installed applications on the client and run through some user activity. This activity is audited and logged to the Ivanti server for approval.
It's time for a long coffee break, the file activity can take a little while to report back to the Ivanti server console. The initial audit results will take a few hours, a full audit will take overnight.
Audited Files:
With the agent installed the 'Win10-01' client becomes available to manage by right-clicking.
Top tip, from Diagnostics its possible to see Ivant client and core logs.
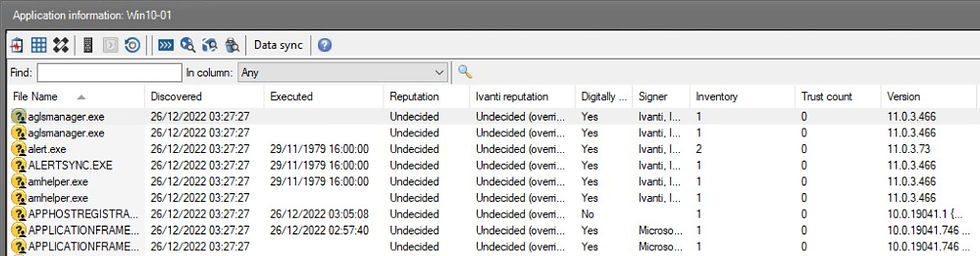
To view the audited files select 'Security and Patch' then 'Application Information'.

As this is a new installation of Ivanti Endpoint Protection the audited files are classed as 'undecided'. It's not as simple as clicking and then approving the files, this can only be accomplished by updating the 'Agent Configuration' settings.
Endpoint Security Policy - Blocking Mode:
The agent has been deployed in learning mode, enabling file data collection to be available in the console.
At this point, those files require authorising and blocking mode enabling.
The easiest method of updating the client from learning to blocking was to update the agent and not just the Endpoint Security policy, having failed repeated attempts.
Right-click the 'Agent Deployment - Initial Config', Copy and then Paste, maintaining the original agent settings.
Rename the agent configuration to reflect its purpose, 'Agent Deployment - Windows Client Blocking'.
Right-click the new agent config, 'Properties'.
Navigate to 'Endpoint Security' via 'Distribution and Patch' and then 'Security and Compliance'.
Click 'Configure...' and in the 'Configure endpoint security setting' click 'New'.
Add a meaningful name to the 'Endpoint Security' wizard.

Click on 'Default Policy' and select ... next to the 'Application control' dropdown.

Click on 'New...'

On the 'General Settings' update the name.

Click on 'Application Protection' and check the following:
Enable application behaviour protections
Prevent master boot record (MBR) encryption
Auto detect and blacklist crypto-ransomware

Under 'File protection rules' select all the options, not all these options may be suitable for an enterprise, and some trial and error may be required.

Under 'Application Protection' click on 'Advanced' and 'Blocking', and remove any checks for 'Learning mode ...'

Under 'Whitelisting' check all options and 'Configure' and select all the script options. Scripts will require authorising to work.
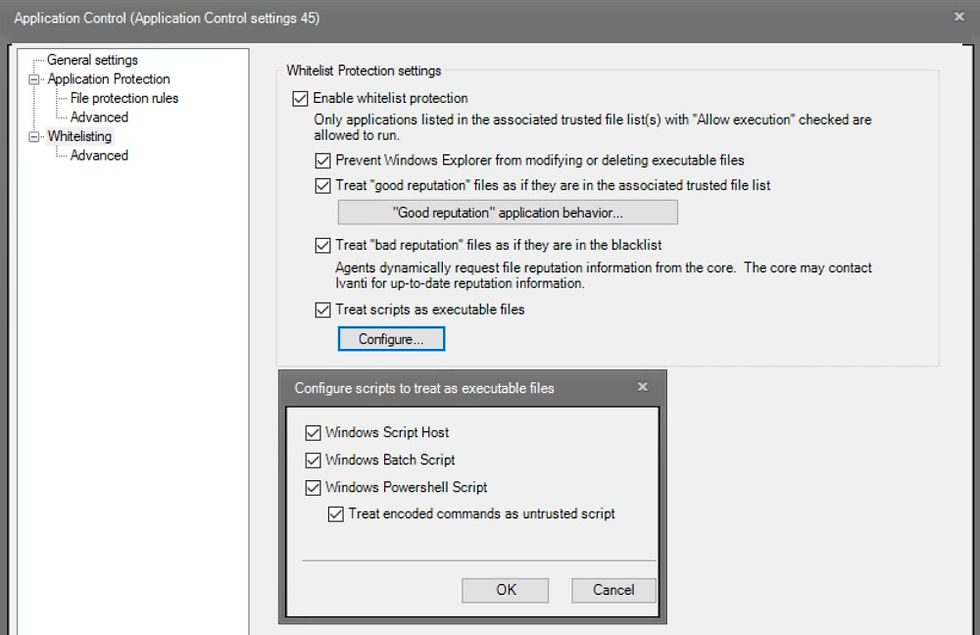
Again on the 'Advanced' page select 'Blocking' and uncheck 'Learning mode ...' save the changes.

Highlight the new policy and then 'Use Selected'.

Enable Microsoft * as a trusted signer, under 'Digital Signatures'.
As Ivanti is authorising files by hash it seems prudent to trust and thus allow all Microsoft files. Ivanti operates at the kernel level, any file not authorised will be denied including system files, it's reasonable to expect blue bends (BSoD) in this case.

Click 'Add...' on the 'Application File List'.

Click 'New'.

To authorise collected from the client click on the yellow circle with a downward arrow.
Click 'Import from other application file lists... '

Check the 'Computer' and select the client.
Ctrl + A to highlight all files and right-click, the 'Override reputation...'

Enable 'Good'.

To ensure that blocking mode is enabled, set CMD.exe's reputation to 'Bad'.

Click 'Next', returning to the Application File List.
Highlight CMD.exe and then click on the pencil, 'Edit Application Files'.
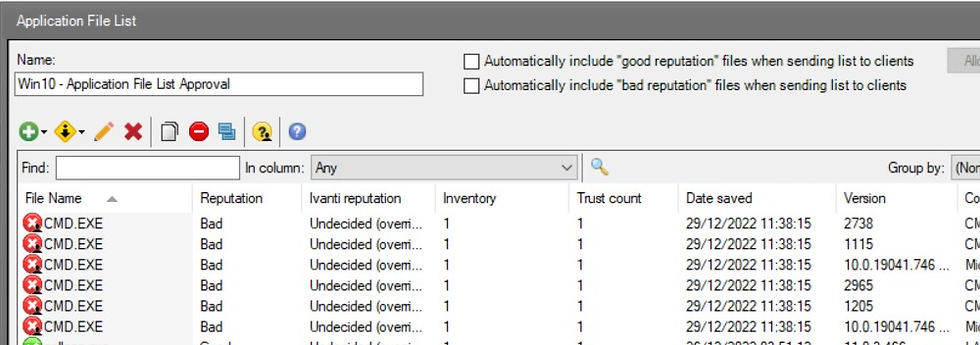
Set the execution from Allow to Block.

OK the changes, close the Application File List, returning to the 'Configure Application File Lists'.
Highlight the new blocking policy then click 'Use selected'.

Update the 'Learning list:' drop down to that of the Win10 approval file list and save the changes.

Ensure the 'Machine Configuration' is configured with the new Windows 10 Client Policy and save the changes.

Point of note: No Dll's were listed in the authorised file list, from previous testing bypassing application protections can be achieved when dll file types arent protected.
Read this (here) where Applocker was successfully bypassed by malware with a DLL file extention.
Deploy Agent in Blocking Mode:
Click on 'Configuration' in the bottom left pane and then 'Agent Configuration'.
In the bottom right pane select 'My Configurations'.

Right-click and properties on the 'Agent Deployment - Windows Client Blocking'
As the target client already has the agent installed a 'scheduled agent deployment' or 'scheduled update to agent settings' should work. I've opted for the agent deployment, removing the old agent and settings alnd installing the new agent with the new blocking configuration.

Click on 'Targets', then 'Targeted Devices', and click on 'Add'.
Select the Windows client with the agent installed and ensure the client box is checked.

In 'Schedule task', select 'Start Now' and then 'Save'.

The Client:
Log in to the client and after about 15 minutes the Ivanti agent with the blocking configuring will have been deployed.
The client is likely to show that the 'Status' is disabled for all components with 'Application Control' also displaying 'Off'.
Reboot the client.
After the reboot the agent should show the following:

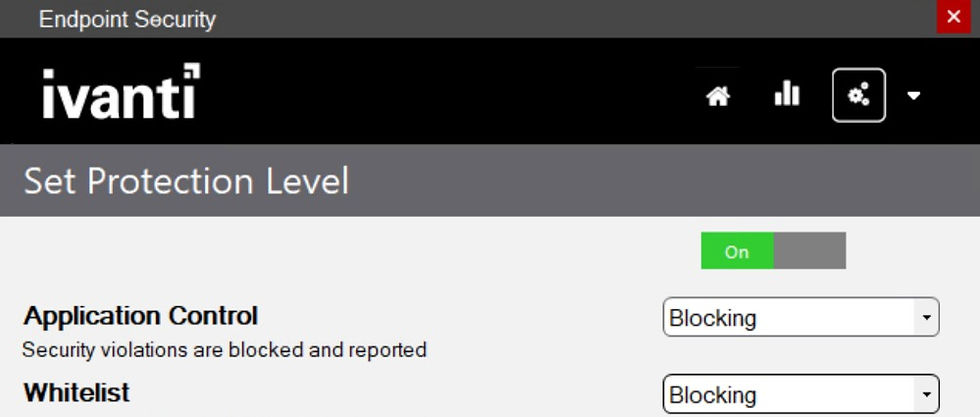
Launching cmd.exe displays the following Ivanti message, cmd is indeed blocked and policy and settings are successfully applied.

The process of creating and deploying Ivanti EP is understood and is repeatable. The next step is to test how effective Ivanti EP is at protecting Windows from various Remote Code Exploits, Local Code Exploits and Reverse Shells following the same patterns used testing Applocker and Device Guard (WDAC). To follow shortly......

Comments